The Quickest And Cheapest Way To Boost Security
Level 1 - NGMI
Welcome Avatar!
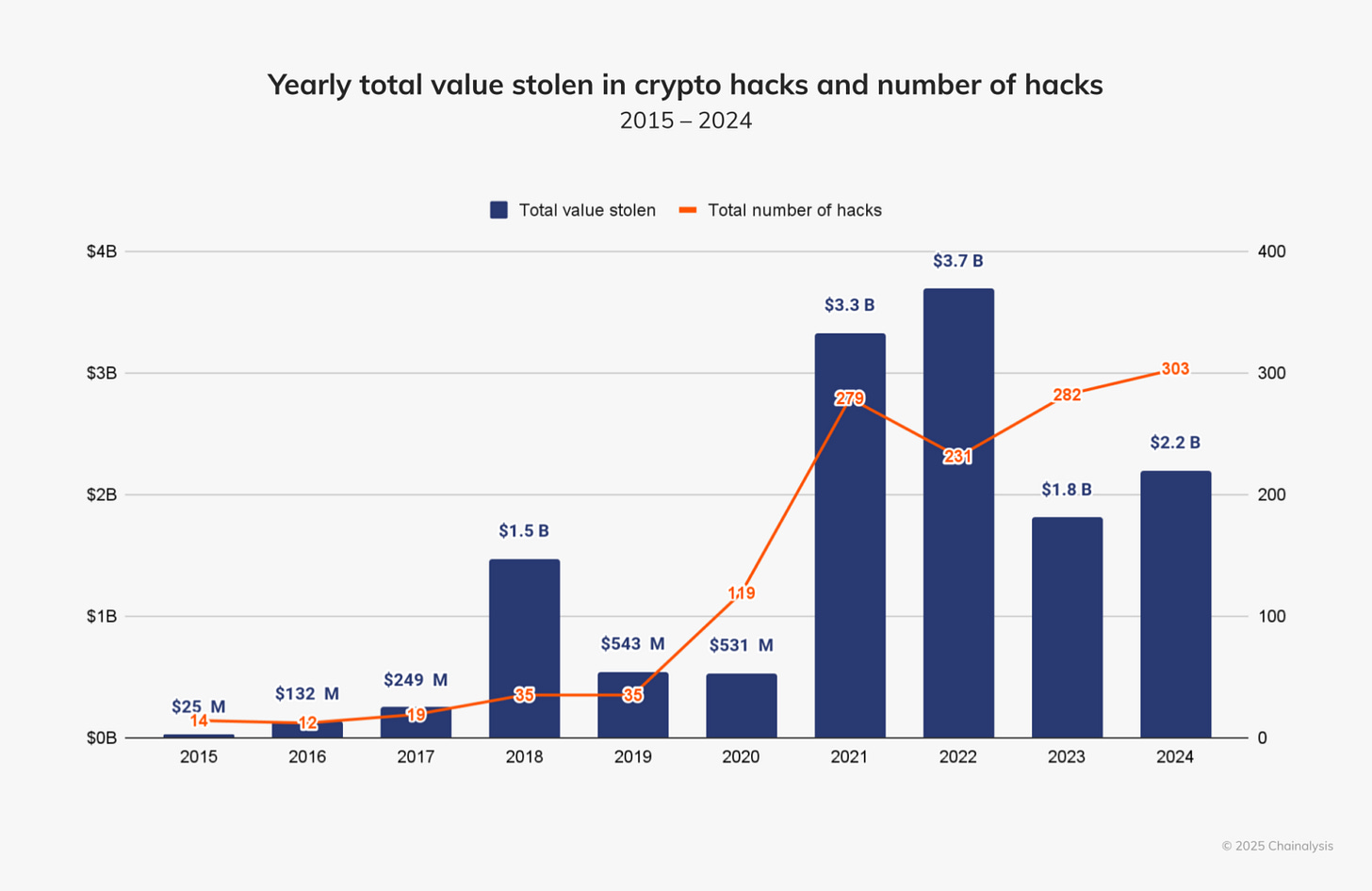
Prices going up isn’t the only bull market happening in crypto. Since our first ever security overview published on BowTiedBull years ago, there has been a bull market in crime targeting computer coins.
Over $2.2 billion of crypto has been stolen in 2025 so far, already eclipsing the entire year of 2024. Personal wallet compromises are the fastest growing share of the total crime ecosystem, making up over 23% of all crypto losses YTD 2025.
Security education is in the DNA of DeFi Education. It deeply pains us when we receive stories directly from readers who have had their wallets compromised, sometimes for very significant sums (7 figures).
As the number of crypto holders grows, the value of crypto holders’ assets grow, and the development of more sophisticated techniques continues, the time to secure your assets and get smart on security is *today*.
The irreversible nature of crypto transactions means that hacked funds are gone forever and there is no way to get that money back unless law enforcement catch up with the hacker before the funds are laundered. In reality, recovery is very rare.
Security is easy to neglect. “That would never happen to me” most people think. But why risk your funds when there is a fairly simple solution?
Today, we’ll discuss the fastest and cheapest way to boost your security - using hardware wallets correctly.
For those who are familar with hardware wallets and want to skip straight to our recommendation, we suggest the Trezor Safe 5.
What Is A Hardware Wallet And Why Do You Need One?
A wallet is a piece of software or hardware which has two functions
store your private key (seed phrase)
sign crypto transactions
If you only used a software wallet - a program on your computer or phone (example: MetaMask) then the private key (seed phrase) is stored on your device. This means if your device is hacked, the attacker can steal all your crypto!
Is this likely to happen?
Yes!
Just last month a major software supply chain attack (explainer) specifically targeted crypto users and affected some of the most widely installed software dependencies in the world (the affected code was downloaded billions of times per *week*).
If you don’t use a hardware wallet, it’s not about if your funds get drained — it’s simply a matter of when.
When you use a hardware wallet, your seed phrase is never shared with your computer or software wallet.
This means when you disconnect your hardware wallet from the computer after signing a transaction, your funds are safe. The seed phrase isn’t stored on your computer or smart phone, so it can’t be stolen by attackers or leaked by badly written software. Your funds are in your control.
Which Hardware Wallets Do We Recommend?
The first thing to do is get your first hardware wallet direct from a reputable provider. We prefer Trezor. There are some tradeoffs to their various models which we will cover here but any new Trezor wallet should be sufficient for most people.
If you have a reasonable amount of crypto - let’s draw the line at $100k - then you’ll want to do some more research into different wallets, such as a Gnosis Multisig.
Both wallets can also protect your online accounts. The FIDO2 standard allows you to use your hardware wallet as a 2 factor device to secure accounts such as Google and Dropbox. This feature alone is worth the money as using SMS for two factor isn’t secure!
Threat model: when considering physical attacks, your risk is different if you travel with your hardware wallet frequently (crossing borders) vs if you keep it in a discreet location safe from a “quick in and out” burglary. If your device is stolen, thieves might attack the hardware to get at your seed phrase (or sell the device to hackers who specialize in this).
I Own A Trezor Model T, Should I Upgrade?
This depends on your threat model. The Secure Element chip introduced in the new Trezor Safe line gives much greater resistance to physical attack than the Model T. However, if physical security / theft is not a large concern then it’s fine to stay on the Model T. If you’re concerned (or want a second wallet for a multisig) get a Safe 5.
Trezor Safe 3 v. Trezor Safe 5
Let’s start with the commonalities. Both share:
the Trezor software suite and open source firmware
NDA-free EAL 6+ Secure Element chip
Shamir Secret Sharing (splitting your seed phrase into fragments to back up to different locations)
tamper evident case and packaging
Safe 3 is affected by a security vulnerability not present in the Safe 5 (see below), but we think the Safe 3 is still safe enough to use. But you must buy direct from Trezor.
The main difference is ease of use. If you transact frequently or care about getting your transaction signed quickly the Trezor Safe 5 is a better option due to the 12 ‘button’ touch screen display. The Safe 3 model has two physical buttons only, which can be fiddly to use (need to simultaneously press and you get kicked to another screen if you don’t hit both at exactly the same time). However the Safe 3 is smaller, lighter, and cheaper making it a good option for occasional use (e.g. part of a multisig quorum/cold wallet).
MicroSD Authentication, Safe 5 Model Only. A bonus feature is the Trezor Safe 5 having a microSD slot, allowing another factor of authentication: something you know (PIN) plus something (else) you have, the SD card. We’re a bit ambivalent about this feature: on the one hand, using a key encryption key stored on the SD card means that it is impossible to extract the private key if only the Trezor is stolen but the SD card remains secure. On the other hand these two items are both likely to be stored in the same physical location for convenience. And should your Trezor be stolen it’s likely you can recover access via your seed phrase and other wallets and move your funds to a new address before the thieves are able to re-sell the device to specialist hackers who *might* be able to exfiltrate the key. For long term storage, advanced users might want to back up the SD card to the cloud (or to servers you control offsite) and then erase the SD card. This would require downloading the data back to the SD card before you use your wallet, and would offer complete protection from only physical device loss/theft.
Duress Wallet
This is an interesting idea: both Trezor wallets support a passphrase, essentially an optional extra word in your seed phrase. You can access either your main wallet (by providing word A) or a decoy/duress wallet (by providing word B). Unfortunately as the existence of the duress feature is public, it is going to be very difficult to convince either robbers or the State that you have provided *complete* access to the wallet. Given the stakes and how hard it is to prove a negative we’d counsel to avoid wallets with duress features if you have the special situation of being vulnerable to sophisticated organized crime linked physical robberies or oppressive State coercion.
Orange Wallets
Trezor still make orange colored “Bitcoin Only” editions of their latest wallet range. These are for customers who only wish to hold and transact in Bitcoin as they cannot be upgraded to support other coins. Maybe “maxis” would prefer to buy these for the small benefit of a somewhat reduced attack surface, as these don’t need software code loaded to support hundreds of different tokens/chains. More code = more bugs.
Summary
Any hardware wallet is better than not using one at all.
The best option for active users is going to be the Trezor Safe 5, and for occasional users or for an extra wallet the Trezor Safe 3. If you have more than $100k in crypto you should have two hardware wallets so you can deploy a multisig for cold storage.
Security
Broadly speaking there’s three forms of attack you need to be aware of:
Social Engineering. The hardware wallet manufacturer tells customers for years that there is technically no way to extract the private key from the secure enclave. Customers rely on this. Then the manufacturer releases a new feature allowing customers to extract their private key to share as part of a recovery service. And this feature can be enabled by a simple software update, proving that the previous product claims weren’t entirely correct. There’s nothing customers can do about this because the hardware is “trust me bro, we’ve signed NDAs so we can’t share exactly how the hardware works for open review”. We aim to avoid this vector.
Supply Chain Attack. The security features built into the genuine wallet don’t matter if your receive a fake which may have almost imperceptible differences in appearance. To mitigate this risk, order directly from the manufacturer and rely on their tamper-resistant packaging.
Nerd Stuff. (aka “needs physical access”). We’re not dismissive about security concerns and we take all valid threats seriously. However, in reality if someone has physical access to your device it’s easy enough for them to replace it with an identical looking decoy device which uploads your PIN over WiFi or Bluetooth and they can then enter the PIN to access your funds on the device they stole. If you have a 1/1 wallet (no multisig) then you need to take care of its physical security. Bank safety deposit box, safe at home, careful when travelling, etc. With this in mind, we don’t think it’s practical to consider attacks which require disassembling the casing, desoldering the microchip, using specialized tools, and then reassembling the device without leaving a trace. Easier to just swap it.
This is however an excellent marketing strategy: employ a Red Team to find flaws in competitor products and publish your findings. Prospective customers aren’t likely to take as much notice of what is required to exploit the device in real life, but the brand benefits from circulating coverage that competitor products are somehow unsafe.
Trezor Safe 3 was affected by a vulnerability which would require physical access, e.g. supply chain attack (Trezor explain the details here). Trezor Safe 5 uses a different microcontroller which is more resistant to voltage glitching attacks.
If you’re concerned even about proof of concept attacks requiring physical access, the safest choice is the Trezor Safe 5 which has no such known vulnerabilities at the time of writing. Trezor provide a detailed list of common security threats, including what they’ve done to reduce risk and what you can do also (e.g. sign the back of your Trezor to make it harder to switch with a fake).
Does A Hardware Wallet Protect Against Everything?
No. If someone tricks you into signing a transaction with your hardware wallet, you’ll still lose your funds. A hardware wallet protects against most attacks where the thieves steal your seed phrase from an insecure computer or mobile device. You still need to follow good security practices like checking transactions before you sign.
Why We Have More Than One
The main reason is multi signature wallets e.g. Gnosis Safe on Ethereum. Anyone with over $100k in crypto should have a “cold” wallet which receives (and sometimes sends) assets but doesn’t otherwise interact with smart contracts and isn’t used regularly (contrast with “hot” wallet). The most secure choice for a cold wallet is a multi-signature solution because compromise of only 1 wallet does not result in loss of funds (unless you created a 1/1 multisig). Also multisig platforms like Gnosis come with extra security features like transaction simulation through Tenderly.
Also consider your hardware wallet could be lost, damaged, or destroyed. If you’ve maintained your seed phrase securely you can still access your funds but you’d have to use a hot wallet since you have no backup. This introduces risk as you may end up downloading a malicious file.
Imagine the sinking feeling - your crypto gone for good!
Either buy a second hardware wallet and use the “restore” feature to make sure both wallets use the same seed phrase, or you can store the seed phrase on something indestructible like a CryptoSteel Capsule or a CryptoTag Zeus.
You can also have multiple hardware wallets using the same seed phrase in different locations in case you want one at home, one in the office, etc. This way you can keep one wallet in a location you are using it actively and a backup wallet to be accessed less frequently.
Finally, we like to diversify risk across multiple wallets. Note - it’s important that you manage your keys securely, otherwise having multiple wallets can introduce more risk.
Where Can I Buy A Hardware Wallet?
For your safety you should only ever buy a hardware wallet direct from the manufacturer to avoid risk of tampering. Supply chain attacks are real. You should not use a reseller like Amazon.
BTB readers can use our affiliate links to purchase their Trezor wallet. We make a small commission at no extra cost to you.
Links:
Buy a Trezor Model 3
Buy a Trezor Model 5
Buy a CryptoTag Zeus - indestructible titanium plate to store your seed
Further Reading
Our software security expert BowTiedIguana has contributed a book’s worth of information for people who want the best security for their computer coins.
Best practice is to either have a separate laptop for crypto, or if you are a more advanced user install QubesOS - see this guide.
Set up a VPN *properly* - be disciplined not to mix identities when using VPN
How to protect against phishing attacks and being tricked by a hacked website.
Security for larger Ethereum wallets - use Gnosis Safe multisig
Affiliate Disclosure: The products recommended here are affiliate links and the proceeds of any income will be distributed as follows: 1) 70% to DeFi Ed team, 2) 15% BTB and 15% Community DAO/Treasury. The income received has *no* cost to you. Since we’ve recommended this for years, collecting revenue for the DAO and getting the DeFi team extra revenue is the priority.
Disclaimer: None of this is to be deemed legal or financial advice of any kind. These are *opinions* written by an anonymous group of Ex-Wall Street Tech Bankers and software engineers who moved into affiliate marketing and e-commerce.
Old Books: Are available by clicking here for paid subs. Don’t support scammers selling our old stuff
How ETH is Staked: Covered (here)
Crypto: The DeFi Team built a full course on crypto that will get you up to speed (Click Here)
Crypto Taxes: We have a suggested Tax Partner and 25% discount code, for information see this post. Crypto Tax Calculator (same as always). You can access CTC HERE and get 25% off your first year for being a BTB subscriber. Yes, this also operates as a ref link. (BTB25) the discount is at no cost to you.
Security: Our official views on how to store Crypto correctly (Click Here)
Social Media: Check out our Instagram in case we get banned for lifestyle type stuff. Twitter will be for money

